About
Security data is constantly evolving. Take back control with Bravura Cloud!
What is Bravura Cloud?
Bravura Cloud is an advanced cloud-native Bravura Security solution providing a powerful, unified interface for leveraging valuable data from the Bravura Security Fabric and third-party applications to get the right access - to the right people - at the right time.
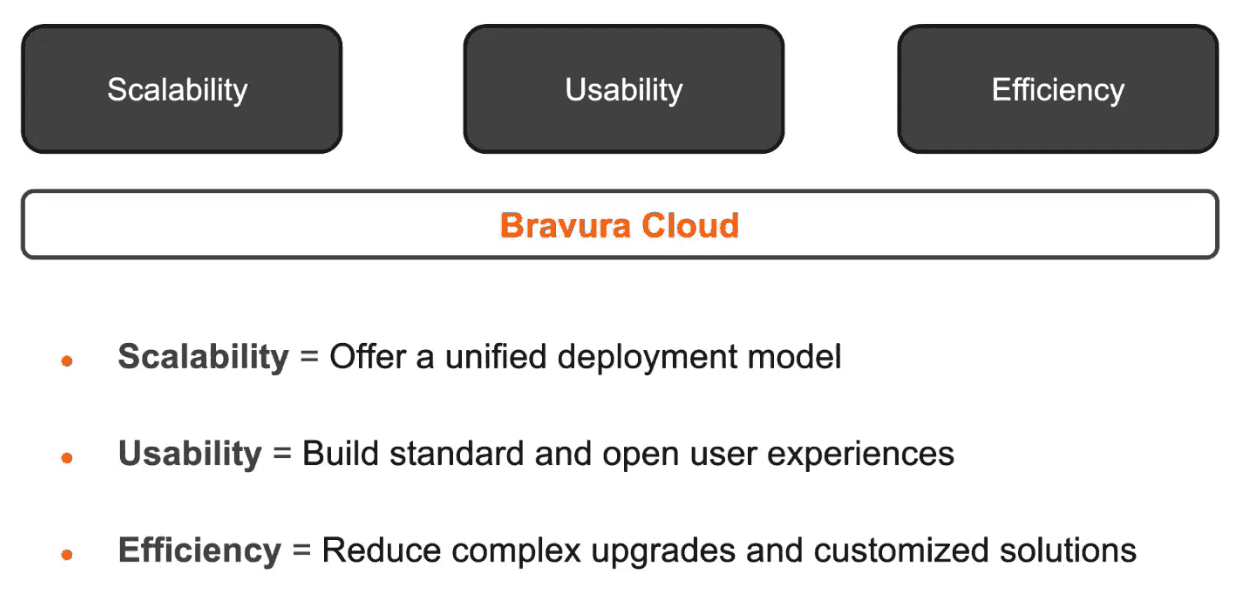
The three pillars of Bravura Cloud are:
New APIs - New User Experiences - New Insight
The modular platform of Bravura Cloud offers foundational and phased, additional modules to further enhance your overall security posture.
Bravura cloud is a modern tapestry of adaptable microservices using industry-standard APIs for real-time monitoring and analysis of your existing security ecosystem:
- A scalable, containerized hosting platform (Kubernetes on AWS)
- A unified API platform (Hasura)
- An advanced data storage platform (PostgreSQL)
- A secure authentication platform (Keycloak)
- An observability platform (Grafana, Loki, Prometheus)
- A Tools-as-a-Service (TaaS) platform (Fusion-io)
- A policy platform (Open Policy Agent)
- A notification platform (TBD)
[**Insert a simple, high-level architecture diagram here]
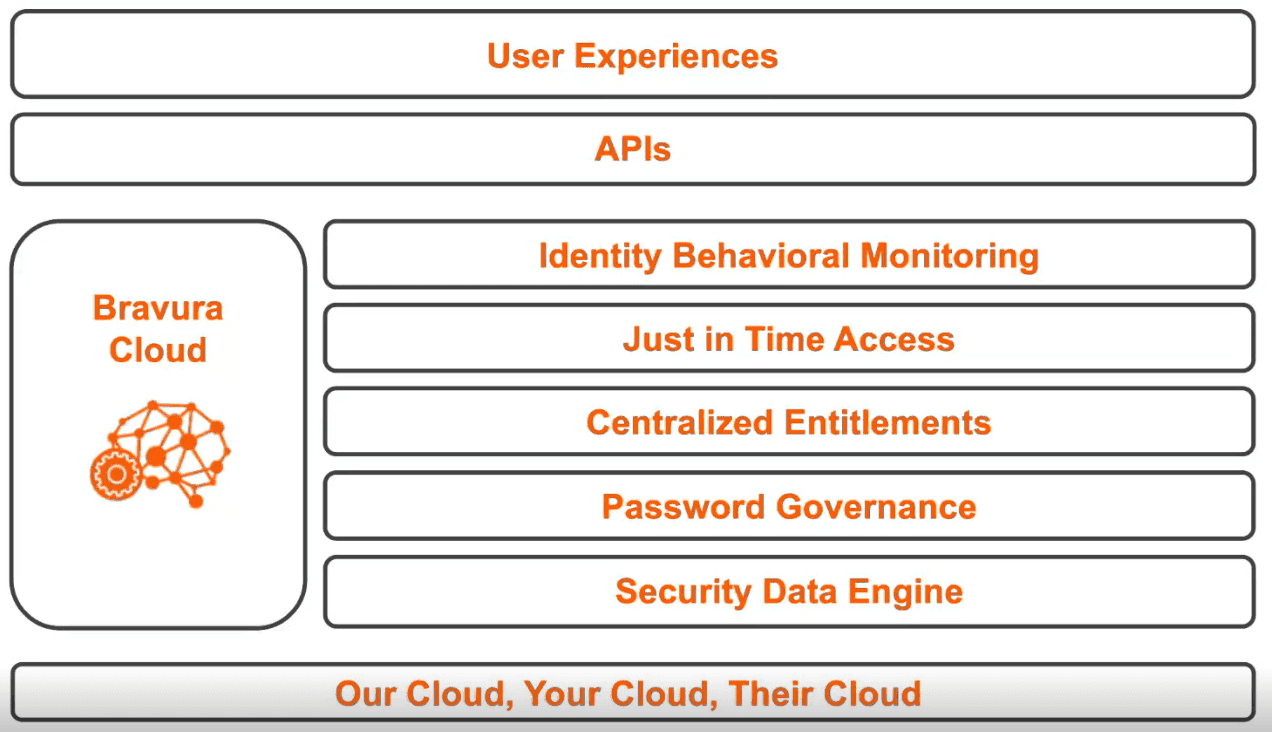
Deployment Models
All sharing the same code base and user experience. You decide:
- Our Cloud - hosted and managed by Bravura Security (SaaS)
- Your Cloud - hosted and managed in your on-premise infrastucture
- Their Cloud - hosted and managed in your public cloud infrastructure
Phase 1: Security Data Engine
The foundational Security Data Engine module allows you to immediately leverage your current investment in the Bravura Security Fabric and other applications by fully discovering, cleansing, inventorying and governing all identities in your ecosystem to achieve a continuous compliance state.
Discover
Unlock visibility into what currently exists in your environment:
- All Bravura Security Fabric products (version 11.0.0+)
- Any IdP, security solution or business application
- Any other application from which you want to extract data
Cleanse
Start a correction process by understanding:
- What users and identities exist?
- What users and identities are no longer required?
- What process should be implemented to resolve issues?
Inventory
Surface data that provides evidence of:
- What users and identities have access to
- The security hygiene of each user and identity
- The ability to put users and identities into a password governance tool
Govern
Take action on risk compliance issues including:
- What risks do you have?
- Are your security practices following industry standards?
- Are regulatory policies being met and followed?
Phases Coming Soon...
Password Governance
- Manage rules and practices for creating, securing and managing passwords
- Comply with regulations
- Secure your digital assets
Centralized Entitlements
- Manage access permissions and privileges from a single, central authority to strengthen security and streamline access management
- Provide visibility for auditing and monitoring, mitigate risks, support scalability, enable quick responses to change and adhere to compliance requirements
Just-in-Time Access
- Provide users with temporary, on-demand permissions only when needed to reduce security risks
- Reduce the attack surface, mitigate insider threats, improve compliance, streamline operations and gain agility to adapt to changing access requirements
Identity Behavioral Monitoring
- Enhance security and threat detection by analyzing user actions and patterns to detect anomalies or suspicious behavior
- Proactively identify and mitigate security threats, including insider threats and unauthorized access to
- Maintain a robust security posture, comply with regulations and respond effectively to security incidents